Multi-signature technology represents a critical security advancement in cryptocurrency management, requiring multiple private keys to authorize transactions. This article examines the technical implementation, security architecture, and practical applications of multisig systems.

Technical Implementation of Multi-Signature Security
Multi-signature protocols establish a collaborative transaction approval framework through cryptographic techniques. At its core, multisig creates an M-of-N requirement, where M signatures are needed from a total of N authorized keys to execute a transaction. For example, a 2-of-3 multisig setup mandates two signature approvals from three possible signers.
The cryptographic process involves:
- Public key generation for each authorized signer
- Creation of a redeem script containing all public keys
- Generation of a multisig address from the redeem script
- Collection of required signatures when executing transactions
- Verification of signature threshold before transaction confirmation
Security Architecture and Risk Mitigation
Multi-signature security introduces multiple layers of protection against unauthorized access and single points of failure. By distributing signing authority across multiple parties or devices, multisig addresses several critical vulnerabilities:
Physical Security: Private keys can be stored in geographically separated locations, making physical theft significantly more challenging. Each key holder maintains independent security protocols, creating redundant protection layers.
Social Engineering Protection: Attackers must compromise multiple key holders to gain transaction control, exponentially increasing attack complexity. This distribution of authority neutralizes many common social engineering tactics.
Internal Threat Prevention: Organizations can implement approval hierarchies requiring consensus from different departments or stakeholders. This prevents unilateral actions by any single authorized party.
Integration with Modern Cryptocurrency Systems
Multi-signature functionality integrates seamlessly with major blockchain networks through standardized protocols. Bitcoin implements multisig through P2SH (Pay to Script Hash) addresses, allowing complex signing conditions while maintaining transaction efficiency.
Ethereum smart contracts extend multisig capabilities through programmable logic, enabling:
- Dynamic adjustment of signing thresholds
- Time-locked transactions
- Conditional approval requirements
- Automated signature verification
Corporate and Institutional Applications
Financial institutions and cryptocurrency businesses leverage multisig for secure asset management:
Custody Services: Professional custodians implement multisig wallets to secure client assets, often maintaining emergency recovery keys in cold storage while using separate keys for routine operations.
Treasury Management: Corporate finance departments use multisig to enforce multi-party approval requirements for large transactions, mirroring traditional banking controls.
Exchange Security: Cryptocurrency exchanges separate hot and cold wallet management through multisig systems, limiting exposure while maintaining operational efficiency.
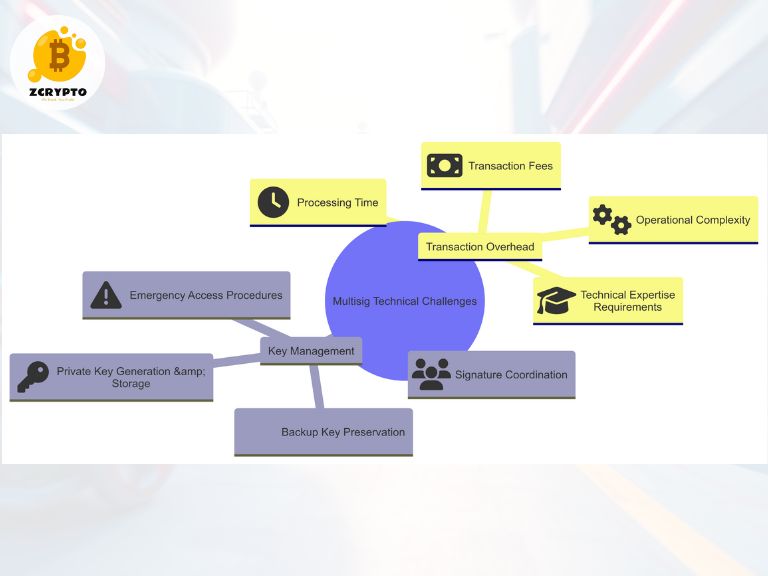
Technical Challenges and Limitations
Implementation complexity introduces specific considerations:
Key Management: Organizations must establish secure protocols for:
- Private key generation and storage
- Backup key preservation
- Signature coordination
- Emergency access procedures
Transaction Overhead: Multiple signature requirements increase:
- Processing time
- Transaction fees
- Operational complexity
- Technical expertise requirements
Advanced Security Configurations
Sophisticated multisig implementations incorporate additional security features:
Threshold Adjustment: Dynamic signature requirements based on:
- Transaction value
- Time of day
- Geographic location
- User authentication factors
Recovery Mechanisms: Backup procedures utilizing:
- Time-delayed recovery keys
- Dead man’s switch protocols
- Multi-party recovery schemes
- Hardware security modules
Implementation Best Practices
Successful multisig deployment requires systematic planning:
Access Control: Define clear authorization hierarchies and approval workflows.
Key Storage: Implement secure storage solutions for all private keys.
Documentation: Maintain detailed records of:
- Key holder identities
- Signature requirements
- Recovery procedures
- Emergency contacts
Testing: Regular verification of:
- Signature processes
- Recovery procedures
- Key accessibility
- System integrity
Operational Considerations
Daily management of multisig systems requires attention to:
Coordination: Establish efficient communication channels between key holders.
Monitoring: Track transaction status and signature collection progress.
Maintenance: Regular review and updates of:
- Security protocols
- Access permissions
- Recovery procedures
- Documentation
Technical Integration Requirements
System architects must address specific technical requirements:
Infrastructure: Deploy secure networks and communication channels.
Compatibility: Ensure wallet software supports multisig operations.
Scalability: Plan for increased transaction processing overhead.
Redundancy: Implement backup systems and failover procedures.
Conclusion
Multi-signature technology provides a foundational security framework for cryptocurrency asset management. Through cryptographic distribution of signing authority, organizations can implement comprehensive security controls while maintaining operational efficiency. The technical sophistication of multisig systems continues to advance, offering increasingly refined security options for both institutional and individual users.


