Mining pools represent a critical infrastructure component in cryptocurrency networks, enabling multiple participants to combine their computational resources for more predictable block rewards. This technical analysis examines the core mechanisms, operational frameworks, and economic dynamics of mining pools in cryptocurrency networks.

Technical Architecture of Mining Pool Operations
The mining pool architecture integrates several interconnected components for work distribution and reward calculation. At its core, the pool server maintains connections with miners through specialized protocols like Stratum V1 and V2. These protocols manage work distribution through standardized methods, handle share submissions from miners, verify contributions, adjust difficulty parameters in real-time, and calculate reward distributions.
Pool operators run full nodes for their supported cryptocurrencies, which allows them to validate blocks and transactions while keeping their mempool synchronized with the network. The technical infrastructure processes millions of share submissions daily while maintaining accurate records for reward distribution.
Mining Pool Reward Distribution Methods
Mining pools implement various reward systems, each based on distinct mathematical models and distribution strategies. The proportional method calculates rewards based on contributed shares relative to the total pool shares within a specific time frame. This creates a direct relationship between mining effort and compensation.
Pay-Per-Last-N-Shares (PPLNS) focuses on recent contributions by considering only the last set of shares before block discovery. This method helps prevent pool hopping and encourages consistent mining participation. The size of the window affects both the variance in payments and the fairness of distribution.
Network Protocol Implementation
Modern mining pools utilize advanced networking protocols to handle the high volume of communications between miners and servers. These protocols optimize data transmission, reduce latency, and ensure reliable share submission verification. The implementation includes sophisticated difficulty adjustment mechanisms that adapt to individual miner capabilities.
Economic Analysis of Pool Operations
Mining pool economics encompasses several key metrics that affect profitability and sustainability. Hash power distribution across the network influences block discovery rates, while difficulty adjustments impact mining efficiency. Transaction fee allocation policies vary between pools, affecting miner revenue.
Operating costs and fee structures typically range from 1-3% of mining rewards. These fees support infrastructure maintenance, development, and pool operator profit margins. The economic model must balance competitiveness with operational sustainability.
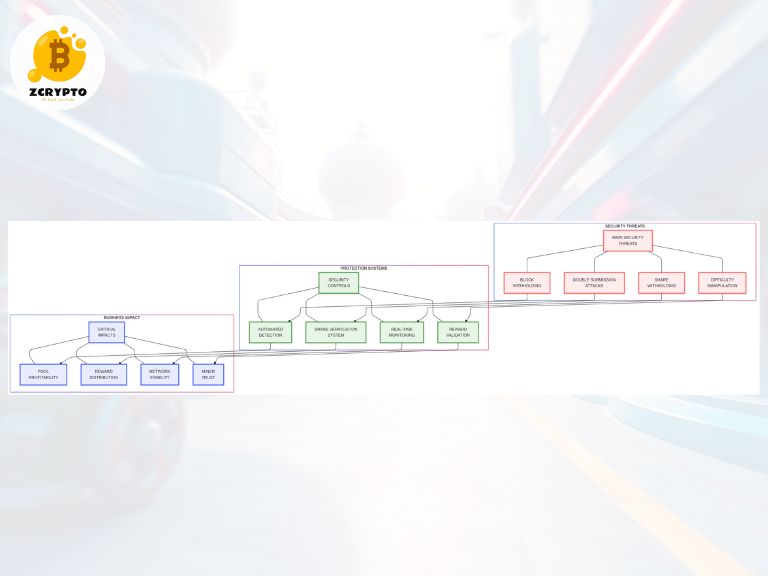
Security Considerations and Attack Vectors
Mining pools must implement comprehensive security measures to protect against various attack vectors. Double submission attacks attempt to claim rewards multiple times for the same work. Share withholding strategies aim to manipulate reward calculations, while block withholding can significantly impact pool profitability.
Difficulty manipulation attempts may try to exploit reward calculation mechanisms. Modern pools implement strict verification procedures and monitoring systems to detect and prevent these security threats.
Current Technical Implementations
Major mining pools employ sophisticated technical infrastructure to maintain reliable operations. Their systems typically include high-performance computing resources, specialized databases for tracking contributions, and load-balanced architectures to ensure high availability.
Real-time monitoring systems track pool performance, detect anomalies, and maintain optimal operating conditions. These implementations often integrate multiple layers of redundancy to prevent service interruptions.
Mining pools continue to serve as critical infrastructure in proof-of-work cryptocurrency networks, balancing technical efficiency with economic incentives. Their implementation requires careful consideration of protocol design, security measures, and reward distribution mechanisms.


