The mempool (memory pool) serves as the transaction staging mechanism in blockchain networks, acting as a temporary storage space for unconfirmed transactions before their inclusion in blocks. This technical analysis examines the core operational aspects, implementation considerations, and critical role of mempools in blockchain infrastructure.

Technical Architecture and Implementation
The mempool operates as a node-specific data structure, maintaining a local database of pending transactions. Each node independently manages its mempool, implementing specific validation rules and size limitations based on network parameters.
Key technical components include:
- Transaction verification modules that perform cryptographic signature validation
- Memory management systems for efficient transaction storage
- Priority queue implementations for transaction ordering
- Network propagation protocols for transaction distribution
- Resource allocation mechanisms for optimal performance
Memory management becomes particularly critical as transaction volumes increase. Nodes must implement careful strategies to handle memory constraints, including transaction eviction policies based on fees and age, along with size limitations to prevent resource exhaustion.
Transaction Processing and Validation
Mempool transaction processing involves multiple stages of validation and verification:
- Initial transaction receipt and basic syntax checking
- Cryptographic signature verification
- Input validation against the current UTXO set
- Fee calculation and minimum threshold verification
- Script validation for smart contract transactions
- Double-spend detection against existing mempool entries
The validation process ensures that only legitimate transactions enter the mempool. Each stage applies specific rules and checks, reducing the risk of invalid transactions consuming network resources.
Network Propagation and Synchronization
Mempool synchronization across the network relies on efficient propagation protocols. When a node receives a new transaction, it:
- Validates the transaction against local rules
- Adds valid transactions to its local mempool
- Broadcasts the transaction to connected peers
- Maintains transaction state information
- Handles re-broadcasting of unconfirmed transactions
This process ensures consistent transaction distribution across the network while minimizing bandwidth usage and maintaining network efficiency.
Performance Optimization and Scaling
Performance optimization in mempool management focuses on several key areas:
- Transaction indexing for rapid lookup and validation
- Memory-efficient data structures for transaction storage
- Parallel validation of independent transactions
- Efficient fee estimation algorithms
- Resource-aware transaction eviction policies
These optimizations help nodes maintain responsiveness and efficient resource utilization under varying network conditions.
Security Considerations
Mempool security involves protecting against various attack vectors:
- Transaction spam protection through fee requirements
- Memory exhaustion attack prevention
- Eclipse attack mitigation
- Transaction replacement rules
- DoS protection mechanisms
Security measures must balance protection against attacks with maintaining network accessibility and transaction throughput.
Operational Monitoring and Management
Effective mempool monitoring requires tracking key metrics:
- Transaction arrival rate and processing time
- Memory usage patterns
- Fee distribution analysis
- Transaction confirmation times
- Network propagation delays
These metrics help operators identify issues and optimize mempool performance.
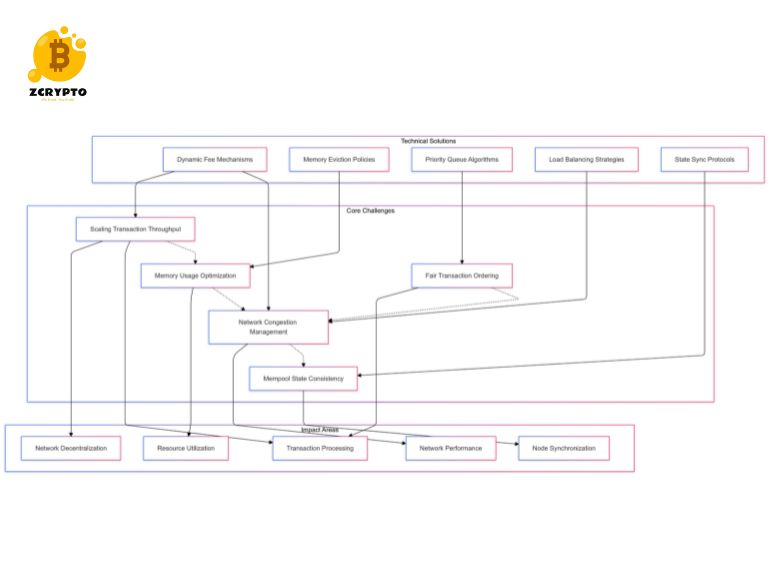
Technical Challenges
Current technical challenges in mempool management include:
- Scaling transaction throughput while maintaining decentralization
- Optimizing memory usage for resource-constrained nodes
- Implementing fair transaction ordering mechanisms
- Managing network congestion during high-load periods
- Maintaining consistent mempool state across the network
These challenges require ongoing technical innovation and optimization to address effectively.
Network Integration
Mempool integration with blockchain networks requires careful consideration of:
- Block template construction algorithms
- Transaction selection strategies
- Network protocol compatibility
- Consensus rule alignment
- Resource allocation policies
Integration must maintain consistency with network rules while optimizing for performance and reliability.
Technical Implementation Considerations
When implementing mempool management systems, developers must address:
- Data structure selection for optimal performance
- Memory management strategies
- Network protocol design
- Security measure implementation
- Monitoring and maintenance capabilities
Implementation decisions significantly impact network performance and reliability.
Fee Management and Prioritization
Transaction fee management within the mempool involves:
- Dynamic fee estimation based on mempool state
- Priority queue management for transaction ordering
- Fee-based transaction replacement policies
- Minimum fee threshold enforcement
- Fee-based eviction strategies during congestion
These mechanisms ensure efficient allocation of network resources and incentivize appropriate fee levels.
Resource Management
Effective resource management strategies include:
- Memory allocation and deallocation protocols
- CPU usage optimization for transaction validation
- Network bandwidth management
- Disk I/O optimization for persistence
- Cache management for frequent operations
These strategies maintain system stability and performance under varying loads.
The mempool represents a critical component of blockchain networks, requiring careful technical consideration in its implementation and operation. Success in mempool management demands continuous optimization of transaction processing, security measures, and resource utilization while maintaining network efficiency and reliability.


